Solution: Fixing “This Site May Be Hacked” Message from Google
Having “malicious code” or automatic redirects on your wordpress website can cause Google to put your in their “blacklist” if you don’t fix the problem soon enough.
Most likely your getting this message because your site has been flagged by Google as malicious or it means that a cyber-spammer has successfully exploited your server/hosting and installed damaging code in your site. Your site is now either blacklisted by Google or displaying a message saying you may be hacked, and every visitor who comes to your site will either be prevented from reaching the homepage or automatically redirected to a an ad. Even search results where your site appears in the Business Listings will be flagged as malicious by Google.
Don’t worry though, we have put together an easy step-by-step guide to help you remove the malicious code by yourself and if you can’t figure it out we also have a service that can remove the malicious code and warning messsage from Google stating, “this site may be hacked” or “this site may harm your computer” from your wordpress installation before you get blacklisted or after depending on your circumstances. We will also show you how to re-submit your site to Google for a site reconsideration/review.
Step 1. Check to see if you have malicious code installed on your site
There are a couple ways to check for malicious code on your WordPress Installation.
1. GoDaddy
If you are hosted with Godaddy just give them a call and they can help you spot the code but they cannot take it out for you. Ours was installed in the index.php area of our website. You can also check for this code by visiting /appearance/editor/index.phpin your wordpress dashboard (You won’t be able to delete it out of there though, you will need to login to your file manager at Goddady – See Below). Here’s what the malicious code looks like:
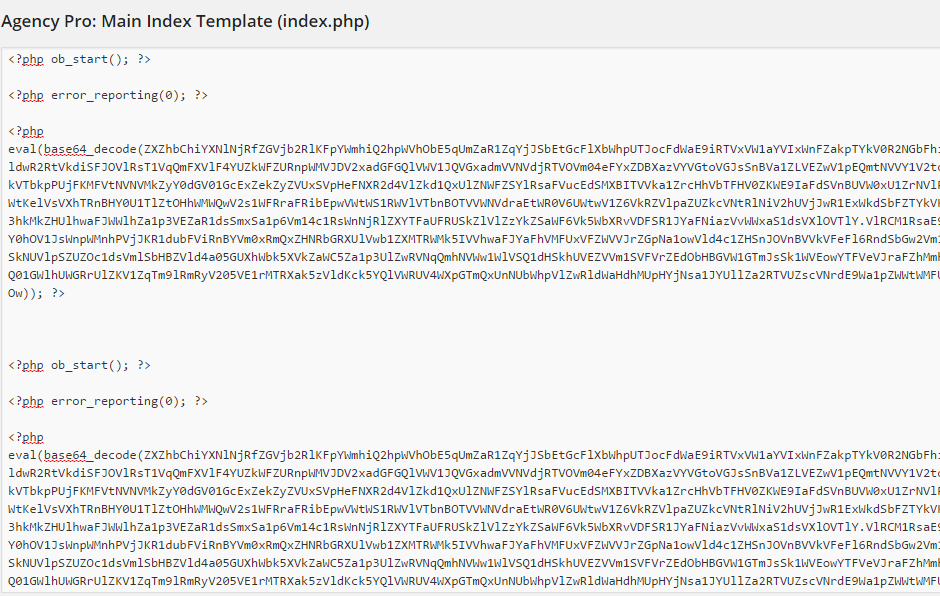
If you are viewing it the source section of your website this same code will look like: <script>javascript redirect</script> and will be at the very top (Hint: There should be no scripts above the head section of your source. Also, no code goes above <?php in the index.php). This is how the code should look normally.
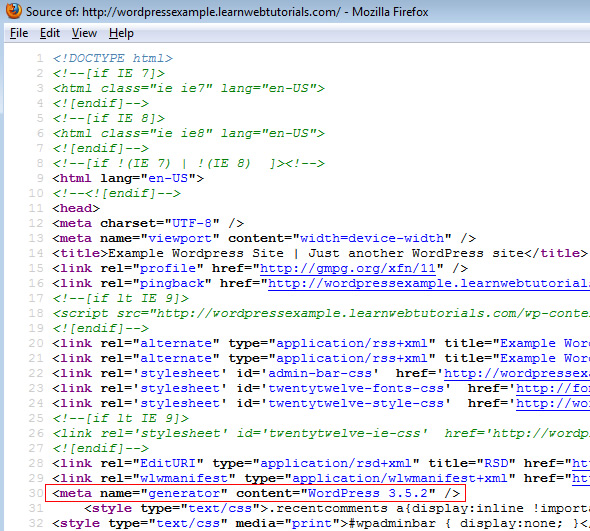
1. (Godaddy Continued) Godaddy can’t help me or the technician doesn’t know what I’m talking about? How Do I remove the Code Myself?
Here’s how to find the file your self. Go to “My Account” – Select Hosting – Click “File Manager” – Make sure your in the “Web Root Section” and you will see all of your core files. Heres what they look like:
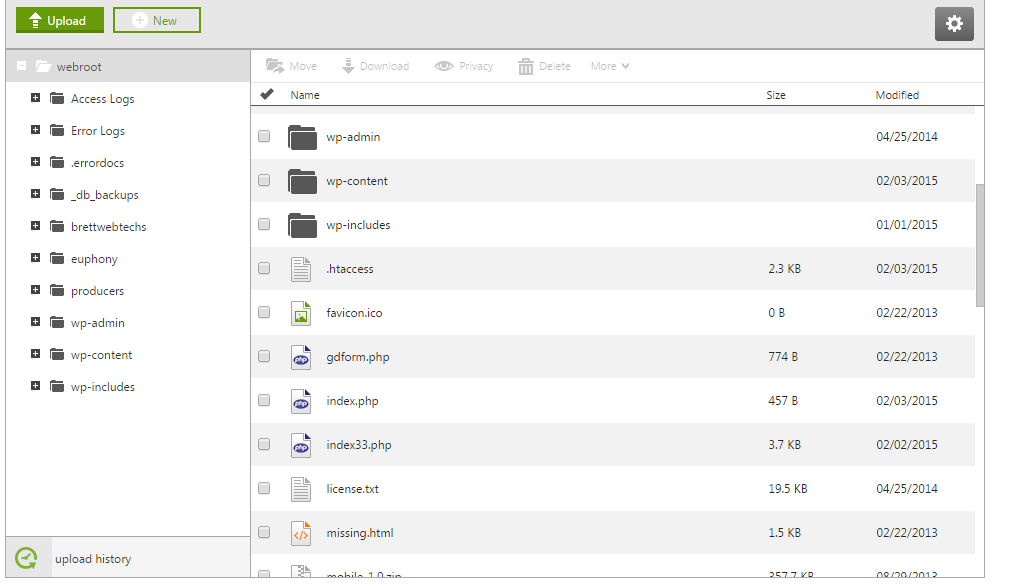
Click on the file that says “index.php” *Remember earlier we said (no code above the<?php in the index.php) This index.php has malicious code in it above the <?php of the code and therefore it is malicious. (Same goes for the header.php – see below)
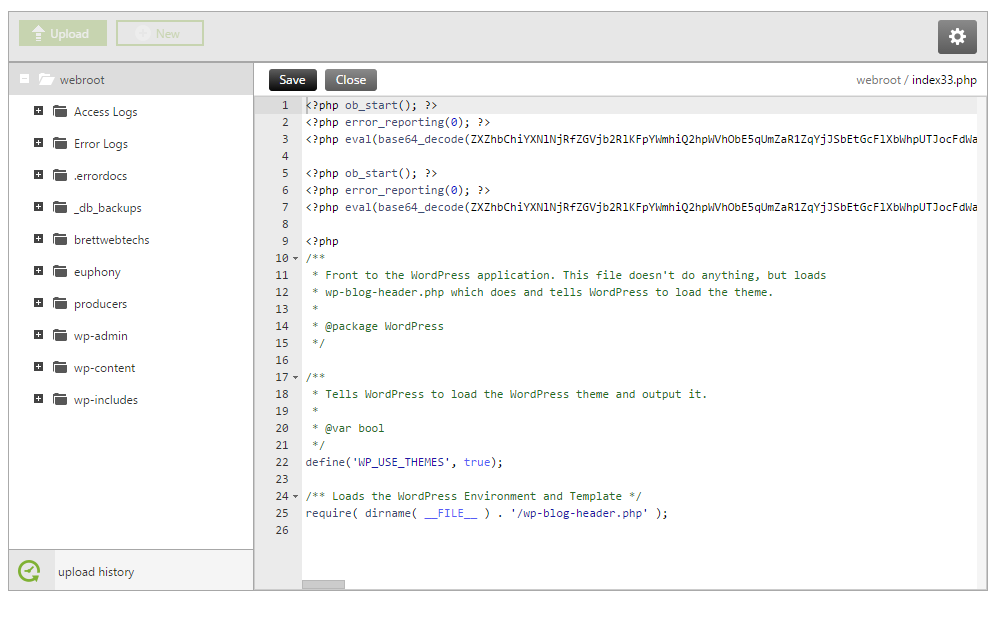
Remove the code and make sure that <?php is at the very top on line 1 of your code and click save. Jump back to your site and try to see if it’s still redirecting. If it hasn’t stopped, the code may be somewhere else. Also, some of these malware codes stop redirecting after a user clicks 1 time so get other people to click on your site from a google search before you decide that it’s fixed. You may be jumping the gun.
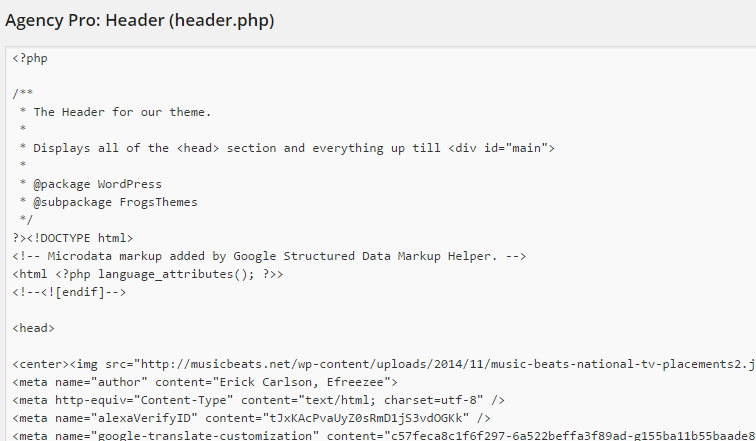
2. Check the Header.php
A normal Header.php looks like this: (No code goes above <?php, so if you have code above there, its probably malicious as well.)
3. Wp-config.php
Heres what a normal wp-config file for wordpress looks like:
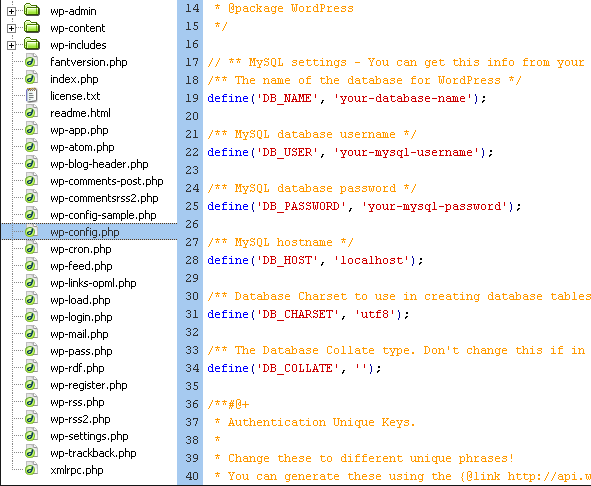
The generic names above will be replaced with the actual URL of your site. If you notice that your URL looks funny or is a completely different URL alltogether then this is where your malware is coming in.
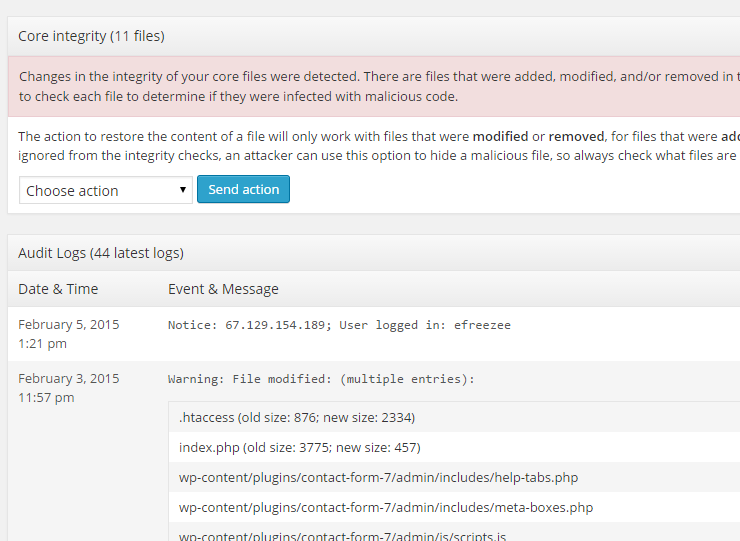
4. Run a Malware Scanner Like Securi Scan
We tried running this plugin and it did show that we had malicious code but not where it was. It seemed like they just wanted us to sign up for their protection first. I wouldn’t suggest using this method unless you absolutely have to. The one benefit about this plugin is that it will log when users log in and make changes so that anytime you see changes from somewhere else you will know that you have been hacked.
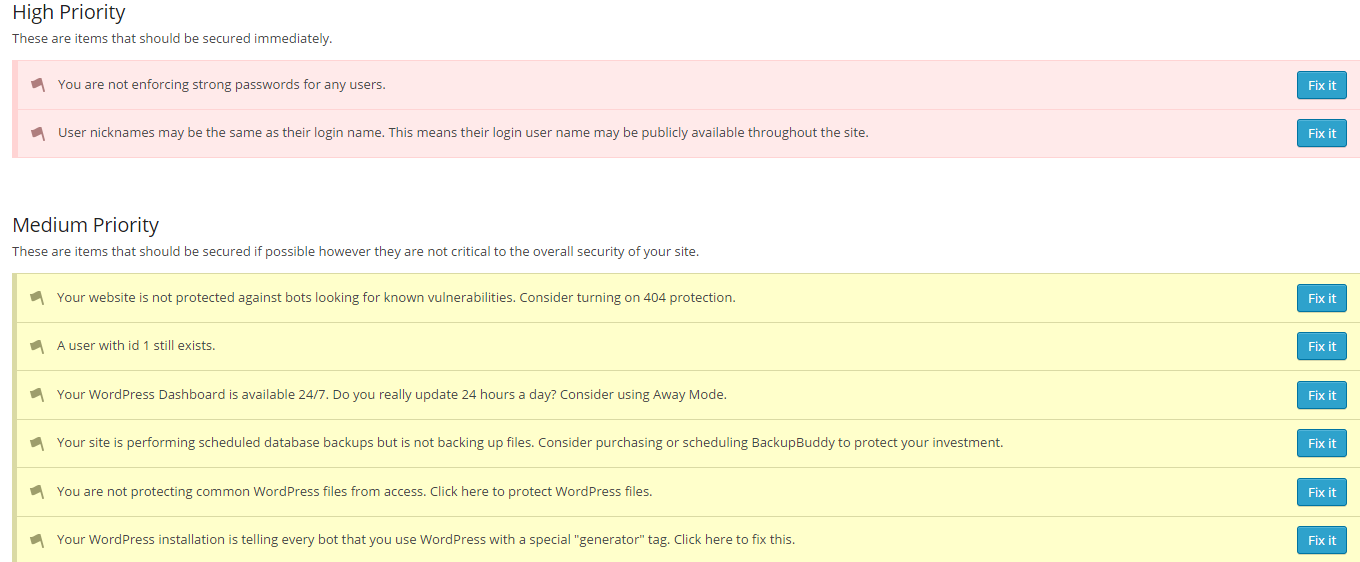
Step 2. Keeping Malware Out for Good
Now that you got the malware or malicious code removed from your site it’s time to keep it out. Here are steps to make sure your malware never comes back:
- Change all your passwords to your wordpress and godaddy
- Update all WordPress Plugins and get rid of any that you aren’t using (Do this for subdomains as well)
- Update all WordPress Themes (Even ones not being used)
- Install a security plugin like “I Themes Security Plugin for WordPress” (Easy – It has a checklist of things you should do to make sure your site is protected)
Step 3. Request Site Review/Consideration from Google
In the final step you will need to request a site review from Google and hopefully they provide a clean bill of health. Just log back into Google Webmaster Tools and visit the Health -> Malware page. Click the link to request a site review. Once Google has deemed you no longer compromised the malware warning messages will start to disappear. This may not happen as quickly as you like but will happen.
Conclusion
I know it can be a frustrating and confusing to get your site hacked but it is not the end of the world. This problem is definitely fixable. If you need expert help removing the malicious code don’t hesitate to give us a call or fill out our contact form.

